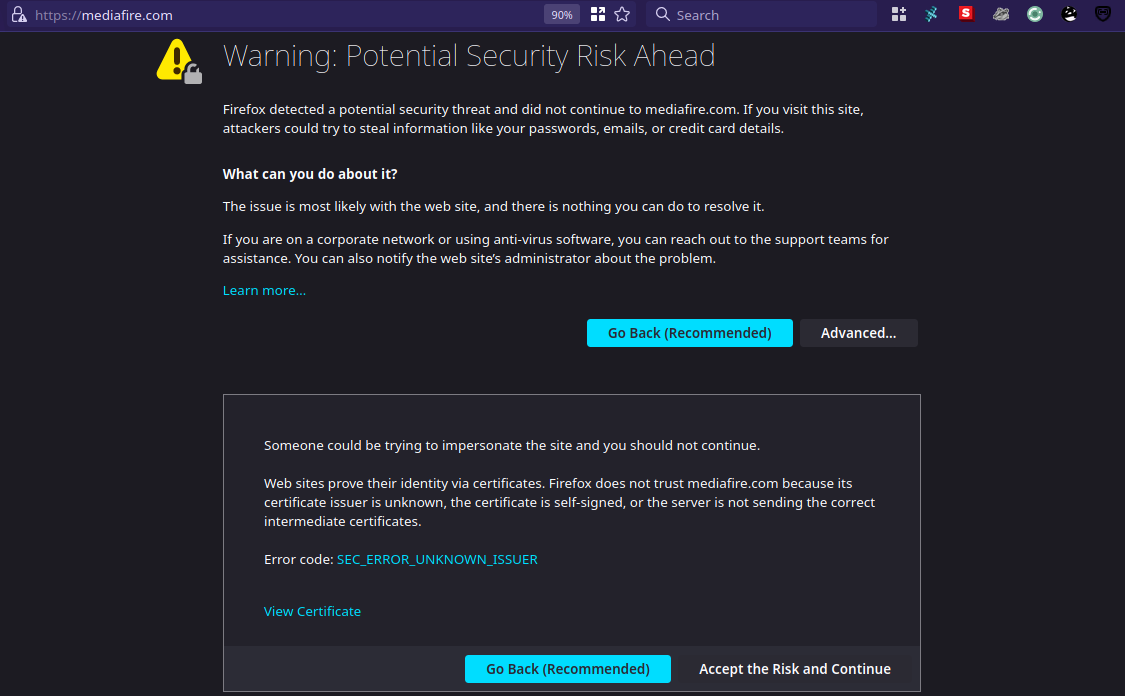
A friend of mine noticed that Philippine ISPs started to hijack connections to certain websites and they are also using a fake SSL certificate. If a user choose the option to continue despite the warning about an invalid SSL certificate, they will see a Philippine government warning and the related Republic Act explaining why they–our ISPs–are hijacking our connection.
Let’s take a look at an example.
MediaFire is a popular file sharing and cloud storage. A file sharing and/or cloud storage service by itself is not “evil” as most governments, politicians, and the corporate world is painting it to be. Unfortunately, as with all services and technologies, there are people who use it for “evil purposes”. This was the basis for the Philippine government [supposedly] ordering Philippine ISPs to hijack the connection to MediaFire, as shown in the screenshot below.
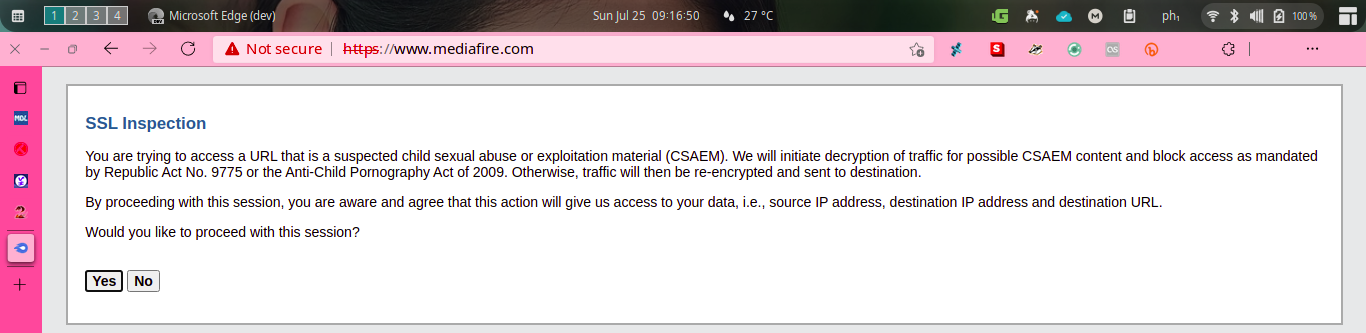
Hijacked connection
Hijacked connection 沿って I’M YourOnly.One です の下で認可された CC BY-SA 4.0 International。
Based on the message shown in the screengrab above, MediaFire is a suspected child sexual abuse or exploitation material (CSAEM)
. They then explained that they will initiate decryption of traffic for possible CSAEM content and block access as mandated by Republic Act No. 9775 or the Anti-Child Pornography Act of 2009.
In other words, they admit that your connection to MediaFire was hijacked and their all-seeing eye is watching you closely.
This is a very bad reality. There is now no doubt that all it takes for Philippine ISPs to intercept our Internet connection is an order from the Philippine government suspecting services and websites of CSAEM and/or whatever other laws they can use to justify breaking the privacy and security of the people.
Google Drive, OneDrive, and Dropbox, probably does not have “illegal content” because they can police their users. But you have to ask the question, how? Could it be they can read all the files uploaded to their storage? We will never know but at least one of those mentioned admitted that they do (it’s even in their Terms).
It is understandable why they are doing this, no good person would tolerate child abuse and child pornography, that is a line no sane human being should ever cross. However, the way they are doing this policing is never acceptable, this is a clear violation of the user’s privacy and hijacking connections is a clear act of compromising the user’s security. No one can guarantee what these ISPs will do with the data they can see. They usually can not be held accountable if one of their “trusted” employee leaks confidential information he or she saw while searching for CSAEM materials. It is easy to say they will never do anything else other than to watch out for CSAEM but clearly, all it takes is a government order and we will never know what they are doing with all the other data.
We all know that we can never trust ISPs, government order or not, so let this be a lesson for everyone in the Philippines: encrypt your files before uploading; and use only services which offers end-to-end encryption; and always use Tor (The Onion Router) or better yet a highly reputable VPN. Our privacy and security matters.
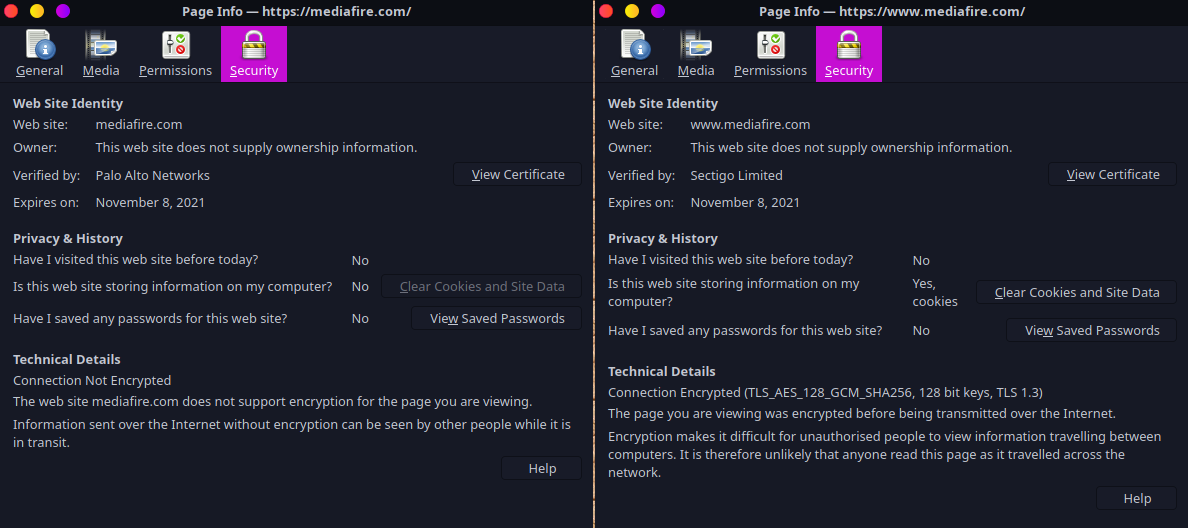
Left: Hijacked connection SSL cert; Right: Encrypted connection and correct SSL certificate
Left: Hijacked connection SSL cert; Right: Encrypted connection and correct SSL certificate 沿って I’M YourOnly.One です の下で認可された CC BY-SA 4.0 International。
It looks like your ISP is using gear from Palo Alto networks to intercept your SSL traffic based on the common name in the SSL certificate.
MediaFire was also informed and they are looking into addressing this.