Once again congratulations on creating a Keybase account. You have joined a growing number of people worldwide who have taken their privacy and security to the next level.
Keybase offers a lot of features, there is end-to-end encrypted Chat, a free 250 GB File storage, a signed hosting, and the ability to easily sign any text, images, and the usual document files. However, there is one feature usually ignored and this feature was one of the hottest when Keybase first sent invites to testers. That is what I will guide you through today.
What is a Keybase Identity?
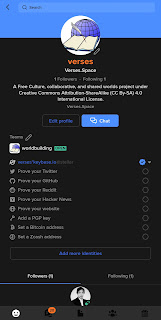
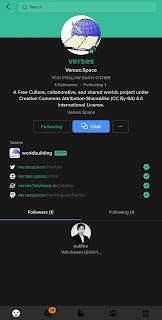
A Keybase identity is a secure online representation of someone (a person) or some entity (an organisation). It lists all the verified online assets (social network accounts, domain names, microblog accounts) of the owner of the Keybase account.
By design, it is near impossible to gain an unauthorised access to any Keybase account without an active “device” (see our previous post). This generally give us the assurance that whoever is updating a particular Keybase account is the actual owner.
However, a bad element can simply create their own Keybase account to impersonate someone. This was solved in two ways by Keybase. The first is by adding third-party identities; and the second is by being followed by other verified Keybase users.
What is a “third-party identity”?
A third-party identity is an account well-known to be under the control of the Keybase account owner. This could be a Twitter account, a domain name, a Mastodon account, or any of the different services supported by Keybase.
By adding multiple third-party identities, a Keybase account’s trust factor—if we can call it that—increases. An impersonator will not be able to add the official Twitter account of their target under their fake Keybase account. They can add their own fake Twitter account or if they successfully gained unauthorised access to the official account. It becomes harder for an impersonator to establish trust to their fake Keybase account when the official one also added a well-known Mastodon account or the domain names he or she owns.
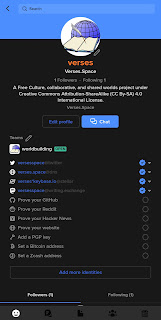
It is impossible for a fake Keybase account to acquire the same level of trust the official account have by that point. Check my Keybase account here and count how many third-party identities are listed. An impersonator will need to have access to all of those social media accounts and domain names before they can add it to their fake Keybase account. Unless they put a gun on my head, they will not be able to do it (especially since I also use two-factor authentication in those accounts).
How to add a third-party identity?
It is quite simple, follow these steps.
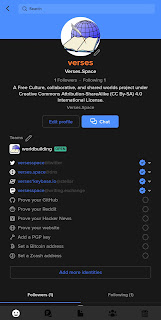
- Launch Keybase and go to your profile
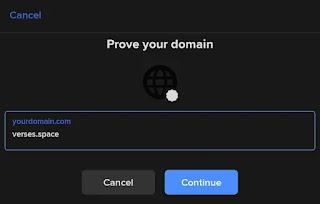
- Click/tap "Prove your Twitter"
- Enter your Twitter username
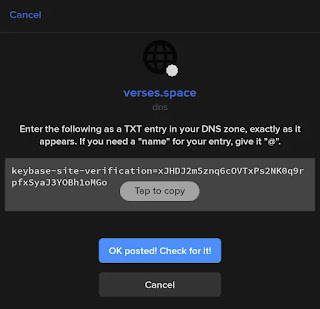
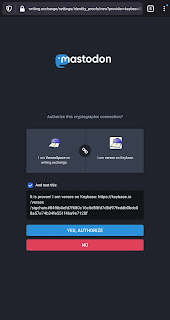
- Copy the text shown exactly as it appears and tweet it; or just click the "Tweet it now" button
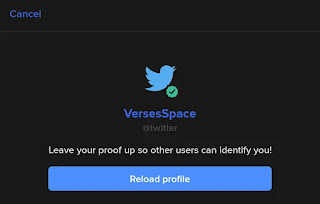
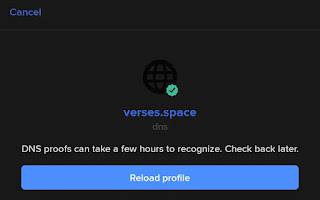
- After tweeting, go back to Keybase if you were not redirected, and click the "Reload profile" button
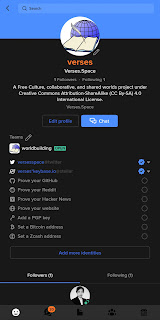
- Your Keybase profile should now show your Twitter as a verified third-party identity
See the verication tweet live.
Verifying myself: I am verses on https://t.co/nSnqrCPeC2. AHx5mSJ2eldtshqT1i1Q47cZJQpJeysDwFEJ / https://t.co/cMMWwDxrsy— Verses.Space (@VersesSpace) June 8, 2020
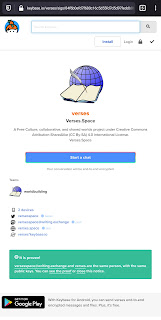
Repeat the process for every third-party account you have which is supported by Keybase. If a third-party service is a shared account, for example domain names or corporate microblogging accounts, it is possible to have multiple Keybase accounts verified. Check the Mastodon account for the Kolverse Worldbuilding and Writing Project, there are two Keybase accounts which verified ownership of it: @[email protected].
Let’s say your Twitter account was hacked or you no longer have access to it. It is imperative to revoke it from your Keybase account. Simple go back to your Keybase profile, click your Twitter account, and revoke it. What it means is you are officially declaring that Twitter account to be no longer yours and any posts from it did not come from you.
It is true there could be a delay to the timestamp when you disavowed your third-party identity to when it was actually compromised, however, remember that by the time we discover our account was compromised it is always after the fact. There is nothing that can be done in that regard other than to revoke it in your Keybase account so you have an official timestamp for record purposes (especially if later you are accused of the content posted by your compromised third-party identity).
Why is being followed important?
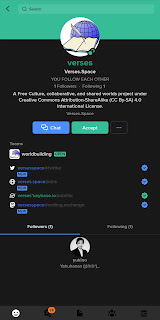
When other Keybase users follows your Keybase account, they are automatically signing your profile or Keybase identity. A follower is virtually saying “I verify this account is who s/he claims to be and the third-party identities s/he added as of this date and time I also verified to be owned by this Keybase user”.
Whenever a Keybase user changed anything in their third-part identities, their followers can optionally verify those changes by visiting the account. If they do, they are signing it effectively saying “I have checked the changes in this account’s third-party identities and have confirmed it as valid”. The more Keybase users who follows and/or verify the changes, the higher the trust factor.
Getting your family & friends to follow your Keybase account and verifying changes in your third-party identities makes it very solid that your Keybase account is actually yours and those third-party identities are also actually yours and have full control. An impersonator or fake account will not be able to build this kind of trust level.
Again, what if a third-party identity was compromised? Revoke it. Your Keybase followers can then visit your profile and confirm the change. By doing so, they are signing or adding their Keybase signature into your revocation update. We can probably say they effectively stand as “witnesses” when you revoked your compromise third-party identity.
There you go. Add all those third-party identities into your Keybase account as a “verified identity” and get your family, friends, and followers to verify those changes. The higher the trust factor of your Keybase account, the stronger and more secure your digital identity becomes.
Part of series: Keybase